
In this article we will explore a pentesting tool called fern WiFi cracker. fern WiFi cracker is an easy to use GUI based WiFi hacker tool which anyone can use. There are no complicated terminal commands required to use this WiFi hacker tool. fern WiFi cracker comes preloaded with Kali Linux. You can also install this WiFi hacker tool in almost any Linux based distro.
fern WiFi Cracker is written in Python. It uses Python Qt GUI library. Program can crack and recover WEP/WPA/WPS keys and run other critical network based attacks on wireless or ethernet based networks as well.
Installing fern WiFi cracker(WiFi Hacker)
If you are already using Kali Linux, you an skip this step. But if you want to install this WiFi hacker tool on your Linux Machine execute the following command.
#sudo apt-get install fern-wifi-cracker
It will install the Fern WiFi cracker.
Finding the targets in fern WiFi cracker.
If you are running Kali Linux or another distro with Fern WiFi cracker installed you can launch it from the menu. You can also launch it from the terminal with following command.
root@kali:~# fern-wifi-cracker
A graphical interface for the tool will open up as shown below. Now first thing you need to do is select your network interface. As you select your network interface, it will enable monitor mode on the selected interface.
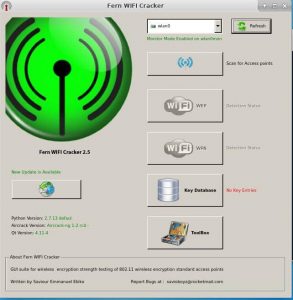
Next step is to click on “scan wireless access point” button. It will start scanning for all the available networks nearby. Once the scanning is finished you can click the WiFi button to see the available network SSID as shown below. Now it’s time to select your target.
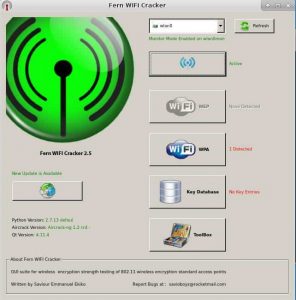
Attacking target
Click on your desired network which you want to attack. Then select type of attack you want to use “regular” or “WPS”.
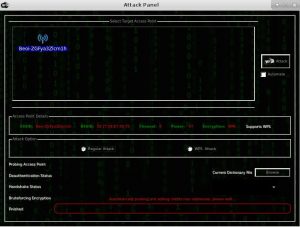
Now go ahead and hit browse button and look for password list file. In order to crack a WiFi password you need to have a password-list which you can use to brute-force the wireless network. You can easily get multiple password text-file on the internet.
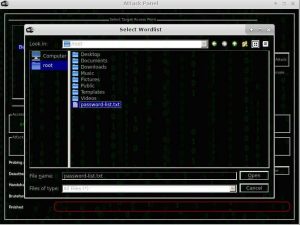
After selecting the password file now it’s time to wait until password for the selected WiFi network is revealed. It may take some hours or even days depending upon the size of the password file and speed of your CPU.
Creating your own password-list or word-list
Creating word-list for password cracking is simple if you know what you are doing. Those of you who have experience in this task know that there are many subtleties to this ‘art’.
Sometimes we may have some valuable knowledge about target’s choice of password or password elements. This Knowledge is gathered by having some recon done on our target, e.g. girlfriend-name, friend-name, birthday, favorite number, etc. We may also know the organization’s policies about the passwords (e.g. minimum 8 characters, uppercase and lowercase, etc.).
In such scenario, we need to create a custom word-list or password-list that reflects our knowledge of the target or the organization’s password policy.
So to create word list for our brute-force attack we will be using a program called crunch. crunch comes pre-installed in Kali. For any other distribution you can easily download it from the software repository.
Let’s start by creating simple word-list for our WiFi hacker tool. Let’s assume that we know that target has passwords between 4 and 8 characters. We can generate all the possibilities in crunch by typing:
#crunch 4 8
When we run the above mentioned command, crunch will show the estimated size of the file which is to be created and then start to create the list.
We can shorten this process based on the acquired knowledge of the target. For instance if we somehow know that the target always uses number passwords between 6 and 8 characters? We could create a complete list of password possibilities meeting this criteria and save them to a file in our desired directory by running the following command.
#crunch 6 8 1234567890 -o /root/num_wordlist.txt
You can generate much more complex word-lists in crunch to be used for this WiFi hacker tool depending upon your recon. But then it would require you to use large amount of processing power. Which will also increase the required time.

Post a Comment