
What is Vulnerability assessment?
When Securing organization’s assets, knowledge is power. In today’s world as businesses grow, their dependency on information technology including the cloud, IoT devices, mobile and social networking grows as well and their cyber risk continues to rise. However vulnerability assessment program can help to identify weaknesses before they become problems. 95% of the cyber attacks exploit known vulnerabilities. Users discover 15000 vulnerabilities each year. The key to responding to such threatfull environment is a robust vulnerability assessment program. Vulnerability assessment is the formal process that identifies and qualifies the security weaknesses including your application software, hardware and network. It will provide you the clean quick report of all the glitches in your IT environment where it needs the attention and where in the list of priorities it lies.
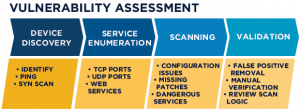
Vulnerability assessment tools
You can also read the list of penetration testing tools here.
10. Nexpose
Nexpose, the unified vulnerability assessment tool is capable of scanning the networks to assess the security parameters of devices running on them. It analyzes the scanned data and processes it for reports. These reports help you assess your security parameters of the network at various levels of detail and patch all the known vulnerabilities. The vulnerability checks assess security weaknesses on each level of a network computing environment, including operating systems, databases, applications, and files. Nexpose can detect malware and worms, identify areas in your IT infrastructure that may be susceptible for an attack, and ensure patch updates and security compliance measures.
9. SARA – Security Auditor’s Research Assistant
The Security Auditor’s Research Assistant (SARA) is a third generation vulnerability assessment tool that is capable of testing your security on every level by interfacing with other security tools. You can integrate SARA with NMAP for reliable system foot-printing. It has very powerful interface for assessing your SMB and SAMBA server configurations. It can adapt to many firewalled environments and strategize the attack vector accordingly. Due to its modular structure it has plug-in facility for third party apps. Integration to the National Vulnerability Database makes this tool extensive vulnerability assessment tool.
8. Enumeration with NSE
Nmap Scripting engine(NSE) is one of the most powerful feature of nmap. Through Nmap scripting engine we can write our own scripts which we can use in performing different networking tasks. You can either write your own scripts in NSE or there are pre-written scripts available. NSE has scripts for authentication, brute-forcing the target, network discovery, dos exploit, fuzzer and malware etc. NSE helps you automate the network security task and quickly enumerate through all the possible vulnerabilities in the network resources.
7. OpenVAS
OpenVAS is a framework of several services and tools that facilitates vulnerability assessment and management. All OpenVAS softwares are free to use. OpenVAS performs remote scans and audits of Unix, Linux, Windows and network infrastructure. It can perform network discovery of devices and assess Operating System, Application, Databases and services running on those devices. OpenVAS provides you nice and elegant Web Interface to use it. You don’t need to know any commands to use this interface. All you have to do is fire up your browser and type the IP address of the machine running OpenVAS and you can test any system on the go.
6. Microsoft Baseline Security Analyzer
Microsoft offers MBSA as a free tool to assess security issues with its products. MBSA scans and checks for any misconfigured and un-patched components on your windows machine. This tool on your system ensures all the settings that Microsoft recommend in order to better defend your self against an attack. This tool also has the capability to scan all the computers on your network. MBSA doesn’t give you any attack vectors but it fixes your system if there are problems with configuration of certain things. So it’s a nice tool to ensure your Windows machine’s security settings.
5. RetinaCS
RetinaCS is an extensive Vulnerability assessment tool that enables you to find and fix defenseless Internet of Things (IoT) devices. IoT devices may be good attack vector for intruders because they have very thin layer of security. RetinaCS allow you to scan and fix any known issue with the IoT devices. It uses the latest CVSS version 3 framework. It scans one or more hosts in minutes via its redesigned host-based agent. RetinaCS alerts you to CWE weaknesses like software security flaws, bugs, and more. It supports Powershell command line and scripting capabilities for starting scans, generating reports, and more.
4. Core Impact
Core Impact pro offers the industry’s most comprehensive multi-vector capabilities. It can leverage various attack vector to mimic a real world attack scenario which makes it one of the widely used vulnerability assessment tools. It provides a web application information gathering wizard to make it easy to target web applications.
With the Wizard we specify the target domain or the IP address as the first step. Core Impact will evaluates the HTML page that provides new URLs to crawl. In the case where web services are found you have the options to import them and to use WS-Security to authenticate against them if needed. After the web services are found then you can launch the web application penetration wizard against these entities. You can install OS injection agent and then escape privileges. After the system is compromised then you can use the compromised system to attack other systems that are reachable from compromised system.
3. SAINT scanner
It is a hybrid tool that comes with both modules vulnerability assessment and penetration testing in the same tool. SAINT (Security Administrator’s Integrated Network Tool) was initially created by SATAN (Security Administrator’s Tool for Analyzing Networks). Back in the 1990s when tools like these were open source, they created security nightmare for some corporations . For example, in the mid-1990s, Hewlett-Packard released a warning to its HP-UX customers that SATAN was coming and they needed to check and strengthen their security.
Unlike those old, cobbled-together collections of hacking scripts – most of them for Unix – today’s SAINT is a paradigm of professionalism in system Security. SAINT has very friendly GUI. It has all the first class functionality that a vulnerability assessment tool should have. SAINT also performs very well performance wise. The integration of SAINT exploit module into the vulnerability scanner module gives you a strong interface for turning vulnerability assessment tool into pen testing tool (as of SAINT8, SAINTexploit is completely integrated into the product instead of being an option). When a vulnerability is found on a system resource, SAINT shows guidelines on the dashboard for exploiting that vulnerability.
2. GFI LanGuard
GFI LanGuard is a great network security scanner and patch management program that acts as a virtual security assistant. It gives you complete overview of your network architecture, provides you risk analysis and helps you maintain secure and compliant network with minimal efforts.
Like any other vulnerability assessment tool first step is to scan the network for security issues. This can be done either by deploying remote agent-less scan or deploying agent. For remote agent-less scan to be performed you simply need to specify your target hosts, select the scanning profile that specify what to look for, enter required credentials accordingly and that’s it. Deployment of agents is also very easy. Deployment of agents are very good for automating network audits and getting improved scan performance because scanning load is distributed across client hosts. Whether you choose to deploy agents to your hosts or scan them remotely, you will always see the most recent result in the dashboard.
1. Nessuss
Nessuss is one of the most powerful vulnerability assessment tools of all time. It implements an HTML web interface for the sake of ease of usability. You can access Nessuss simply via your web browser. It’s a cross platform tool. Supported by Linux, Windows, Android and Mac and full set of features are available across all the platform.
You can put Nessuss on your network and define list of IP addresses then discover vulnerabilities. You can also provide credentials for local machine. It will report on client software such as JAVA, Adobe Flash and Internet Explorer etc. which is incredibly handy and provides both aspects of vulnerability on your network. So you can detect what is available on networking listening ports and what is installed on local systems that might also be vulnerable. Nessuss will use credentials log into the target system. It can also review the settings on that system and compare to the known standards such as PCI, CIS Benchmark, and SCAP etc.

Post a Comment